Connect with us

12 Essential Cybersecurity Practices for Remote Teams in 2021
You’ve hired your remote team, scheduled your projects, and planned your workflows.
You’ve heard security terms like virtual private network and Internet of Things, but you’re not quite sure what they mean or what to do about them.
You’ve had virus protection software on your devices before, but you’re pretty sure it’s expired by now.
The last to do on your list is set up a cybersecurity plan, but you’re not sure where to start.
Thankfully, we’ve got just the thing you need.
In this article, we’ll cover 12 essential cybersecurity practices your remote team needs to thrive in 2021.
Let’s take a look.
Table of Contents
- 1. Use a virtual private network (VPN)
- 2. Secure your workflows
- 3. Use secure HR software
- 4. Use antivirus software
- 5. Commit to having ongoing security training
- 6. Create a secure document signing and sharing process
- 7. Improve password management
- 8. Consider using biometric security technologies
- 9. Create a risk-assessment policy/approach
- 10. Manage IoT security
- 11. Take a proactive approach to phishing
- 12. Issue secure devices or use virtual desktops
1. Use a virtual private network (VPN)
A virtual private network acts as a protected tunnel within another one of your networks. Since all data stays within the tunnel, no one outside the VPN can access it, and your data never leaks onto the web.
VPNs also unlock restricted content without affecting the internet speed on your team’s devices.
By providing your team access to a VPN, your data stays safe and secure on multiple servers and devices.
When researching VPNs, look for one that matches your specific needs. Check out reviews like this NordVPN review to help you understand their features and how they can best serve your needs.
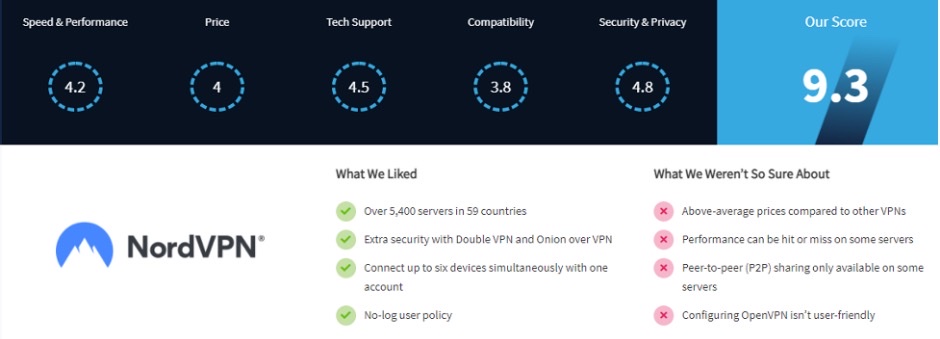
Also, be on the lookout for a VPN that offers customer support 24/7 and international servers if you have an international team.
2. Secure your workflows
From accepting work orders to assigning projects, efficient workflows help cross-functional teams be as productive as possible.
But remote teams have purely digital workflows. If automation or a platform gets stuck, the workflow is interrupted.
That’s why it’s essential to have cloud-based workflows that secure your processes and save new updates in real-time.
Having workflows in the cloud requires employees to follow data security standards set by the company. This may include signing NDAs and installing specific security software on devices.
3. Use secure HR software
Making sure your HR software protects your employees’ personal data is an essential cybersecurity practice.
HR teams often handle sensitive data that can lead to serious legal trouble if compromised. HR employees must have a way to do their jobs and access necessary data without compromising on security.
When choosing HR software, look for one that secures data about:
- The employee onboarding process: Setting up interviews, presenting offers, signing new hire paperwork and contracts
- Employee benefits: Paid time off, insurance options, employee rewards
- Employee financials: Bonus structures, compensation plans, salaries, stock, and pension plans
Outsourcing these responsibilities to a PEO company can be a game-changer for your company. The companies have strict processes and protocols in place to ensure compliance with data security and employee privacy.
Nelson Sherwin, manager of PEO Companies, finds that many companies are happy to have someone else take over these processes, “An idea I had would be to focus on the consequences for business owners who screw up admin and HR tasks whilst trying to save a few pennies.”
4. Use antivirus software
Antivirus software is a cybersecurity tool that protects against ransomware, phishing, malware, and viruses on hardware.
For a remote team, every employee needs high-level protection on any device they use for work.
To ensure everyone on your team installs antivirus software, send them individual access to the software you want them to use. Then, have IT do a remote check to ensure that all employee devices have the antivirus software installed.
5. Commit to having ongoing security training
As technology advances, so do cyber crimes — which means that security measures can change at any time.
From copying passwords to breaking into bank accounts, cybercriminals stop at nothing to get what they want.
But with ongoing security training and remote support, your team is prepared to handle security breaches of all kinds.
When planning a security training schedule, get with your employees to decide on the best form of training and whether or not to administer it as a group or individually.
As technology advances, so do cyber crimes — which means that security measures can change at any time. From copying passwords to breaking into bank accounts, cybercriminals stop at nothing to get what they want.
6. Create a secure document signing and sharing process
Working remotely means onboarding clients, vendors, and employees without seeing them in person.
Instead of handing out physical contracts and pens, you’ll be administering digital paperwork. Instead of meeting at a coffee shop, you’ll be meeting on video calls.
From NDAs to vendor agreements and client contracts, your team will have to keep up with paperwork without sacrificing security.
When setting up a secure document signing process, consider using contract management software.
Contract management software like PandaDoc and Signaturely encrypts and secures documents from lurkers. It also keeps documents in order and guides users through the digital signature process, so all forms are signed and dated correctly.
When sharing sensitive documents, use private documents with assigned permissions and password-protected PDFs. Be sure to train your team to do the same.
It’s also important to train your team to avoid using their personal email accounts or devices when sharing files and collaborating.
If email is the only option, train your team to use email verification tools to make sure all email addresses are valid and safe.
And finally, make sure to encourage your team to report any suspicious attempts or security breaches.
7. Improve password management
Poor password management systems continue to plague remote businesses today. In 2021, improving password management security is imperative.
To improve password management, start by creating a single sign-on (SSO) path for every platform or app your team uses — check out the tool NordPass for this.
Then combine SSO with multi-factor authentication to immediately eliminate a massive amount of risk.
Here are some other quick password security tips:
- Create thoughtful passwords with a variety of characters, numbers, symbols, and capitalization
- Use PAM solutions and password vaults to prevent unauthorized users and simplify password management for employees
- Use a different password for each account
- Require routine password changes
8. Consider using biometric security technologies
Biometric security technologies verify system and network users using voice recognition, fingerprint scans, facial recognition, gait analysis, and palm biometrics.
For instance, using your thumb to access your smartphone’s home screen is biometric security at work.
What makes biometric security work so well is that no two individuals have the same biometric features. So, if an unauthorized individual tries to access information, the identification system will identify that they’re not a recognized user.
9. Create a risk-assessment policy/approach
A cyber risk is the likelihood of your company suffering disruptions to business operations, sensitive data, or financials. Cyber risks are ranked from zero, low, medium, and high risk and can result in data breaches.
Some examples of cyber risks include:
- Phishing
- Cyberattacks
- Malware
- Ransomware
- Insider threats
- Data leaks
Conducting a thorough risk assessment is the only way to know what potential cyber risks and vulnerabilities your company might face.
Cyber risk vulnerability assessments are used to identify, estimate, and prioritize risks surrounding your company’s assets, employees, operations, and information systems.
Risk vulnerability assessments are based on answering the following questions:
- What are the relevant threats and their sources?
- What reputation or financial damage would this cause if breached or made unavailable?
- What’s the likelihood of exploitation?
- What’s the likelihood of cyber threats, cyber-attacks, or security incidents that could impede my business’ ability to function?
- What are my company’s risk targets and boundaries?
- What are the external and internal vulnerabilities?
- Are there any high-priority security risks?
- How can I cost-effectively reduce these risks?
- When creating a risk assessment policy/approach, start by deciding how often you want to conduct the assessment. Then, choose which tools and team members you’re going to use to make the assessment as smooth as possible.
10. Manage IoT security
The Internet of Things (IoT) refers to the network of physical objects/things that are embedded with software, sensors, and other technologies that connect and exchange data with each other. These ‘things’ can range from household objects like alarms to sophisticated tools like chatbots.
Now that people can connect objects they use every day to the Internet, there’s seamless communication between the Internet, people, and things. But that poses a large risk to remote companies with employees who may work from home near these devices.
IoT devices — especially doorbells, security cameras, office equipment, and smart door locks — have access to some of your team’s most sensitive information.
To secure IoT data against malicious intruders, here are some security best practices:
- Conduct IoT penetration tests to understand your team’s IoT risks
- Plan your strategy based on the risk insights you analyzed
- Have all team members install firewalls, improve passwords, and encrypt IoT data
- Supply team members with secure and current routers and ask them to enable the firewall
- Train your team to use end-to-end encryption for resting data and data in transit
- Train your team to use proper authentication, so only trusted connections have access to endpoints
11. Take a proactive approach to phish
Take a proactive approach to phish by educating your team about what to look out for and how to prevent it.
Cybercriminals use phishing techniques — spam emails and phone calls — to collect sensitive information about team members, steal their credentials, or infect their systems.
This often happens when a well-meaning employee unconsciously helps perpetrators get into your system.
To protect your team against phishing:
- Train your employees about common phishing techniques and how to handle them
- Make sure all employees have properly configured spam filters on their work devices
12. Issue secure devices or use virtual desktops
Issuing secure devices or using virtual desktops is the ultimate level of security protection.
Next-generation firewalls and the best malware tools work — but once devices aren’t protected by a corporate network, security is up to each individual employee.
Let’s review two quick options to solve this issue.
Issue secure devices
By using a teleworker gateway, corporate security features extend into employees’ homes to help separate the home into business and nonbusiness networks. These devices also build secure VPN tunnels so employees don’t need to update their VPN software continuously.
Use virtual desktops
An alternative to issuing corporate laptops is using virtual desktops. Virtual desktops let you launch a business OS that looks and operates as if it’s native to the user. But really, the desktop is being streamed from a secure private data center infrastructure or the public cloud. While there are many reasons to choose this option, businesses like to use virtualized desktops for data loss prevention.
Ready to be proactive about cybersecurity?
Remote teams depend on their networks, systems, and operating devices to collaborate, meet, and operate.
When remote teams don’t prioritize cybersecurity planning, they put their business at great risk for cyber threats, cyber-attacks, and security breaches.
To ensure your remote team has all the tools it needs to thrive, take a proactive approach to cybersecurity.



.jpg)
.jpg)



